What is iCloud?
iCloud is a well-known cloud storage and backup service offered to Apple users by Apple company. It is built into every Apple device: iPhones, iPod touches, iPads, Macs, Apple watches, etc.
Each user is entitled to 5 GB of space for free and you can also purchase a subscription if you need more storage space. When needn't, head to downgrade iCloud + plan in one go.
After activating iCloud with Apple IDs, users can store their photos, videos, music, notes, files, contacts, Reminders, messages, and more on iCloud, and sync all the stuff across their devices. So, they can access their data through any of their devices.
Besides, iCloud has a feature called Family Sharing, which lets you share music, books, apps, and more with your family members.
Is Your iCloud Data Secure?
First, let's take a look at iCloud's encryption mechanism. Mainly, iCloud protects users' information in two major ways.
1. AES-128 Bit Encryption
AES-128-bit encryption is a basic technology in the security industry. Although AES-128-bit encryption goes in line with the industry standard, it is actually the lowest standard in the data security industry. It provides weaker encryption and is much less secure than AES-256-bit encryption.
2. End-to-End Encryption Combined with 2FA
End-to-end encryption bonds with each of your approved devices. In this way, your data is locked with extra keys generated on those trusted devices. Each key maps a device. Since your devices are unique, the keys are unique too. 2FA is a verification method that requires you to provide two different codes in two steps for identity authentication.
In the case of iCloud, you need to input the normal password to unlock the cloud end. This is the first step. Then, for the second step, you are required to input a six-digit code to unlock your device end. When both two ends are unlocked, you can continue to visit your iCloud data.
3. Drawbacks of iCloud's Encryption Mechanism
1. Limitations to iCloud's end-to-end encryption. Apple doesn't cover all your data with end-to-end encryption. It only covers "sensitive" information including Home Data, Health Data, iCloud Keychain data, and Payment information. So, if you've stored truly sensitive data like personal notes, photos, reminders, and messages in iCloud, beware.
2. Prerequisites to iCloud's end-to-end encryption. To validate end-to-end encryption, you need to:
- ALWAYS turn on 2FA for your Apple ID.
- ALWAYS keep your iOS system and related Apps up-to-date. Some users may not turn on the 2FA; some users simply don't want to upgrade their Apps or iOS.
These cause inconveniences.
3. Other loopholes. Loopholes exist in some built-in Apps like Find My iPhone. They can be leveraged by cybercriminals. For instance, an invader can use black tools to hack your iCloud passwords with unlimited attempts through Find My iPhone, because the App has a bug that allows unlimited password attempts.
In recent years, some celebrities got their private photos stolen and published online due to such invader attacks. In fact, these attacks are happening every day to ordinary people, too.
Now you can see from the above analysis: that iCloud's encryption mechanism is not secure and strong enough. So, is there a better way to protect your iCloud data? Of course yes—using reliable third-party encryption software can really help!
Why Do You Need iCloud Encryption Software?
Third-party iCloud encryption applications cover your data with flawless protection. They have two major advantages.
First, they bring you convenience. Through several mouse clicks or finger taps, the selected files and folders are encrypted. More impressively, the encryption process is often on the fly, which means you will not be influenced by the encryption when you're working with your files in the iCloud drive. You work as usual; the software encrypts your data backstage.
Second, they have high reliability. iCloud encryption applications cover your data with an additional security layer. They adopt AES-256-bit encryption, which gives you the highest level of data security. Plus, they enable you to keep your data fully under your own control.
Unlike iCloud's end-to-end encryption, their end-to-end encryption takes the "zero-knowledge" paradigm. This means those encryption applications are just focusing on encrypting and protecting your data—not a slight piece of your data including the encryption key will they collect. You give them zero information, they offer you strong and flawless protection.
Well-ranked iCloud encryption applications are Boxcryptor, Kruptos 2, Cryptomator, etc. They are compatible with Macs, iPhones, iPads, iPod touches, Android phones, tablets, and Windows PCs.
Dropbox Encryption: Everything You Need to Know
This article will evaluate Dropbox security from a technical perspective and talk about how to encrypt your Dropbox files/folders from hackers and unauthorized access. Read more >>
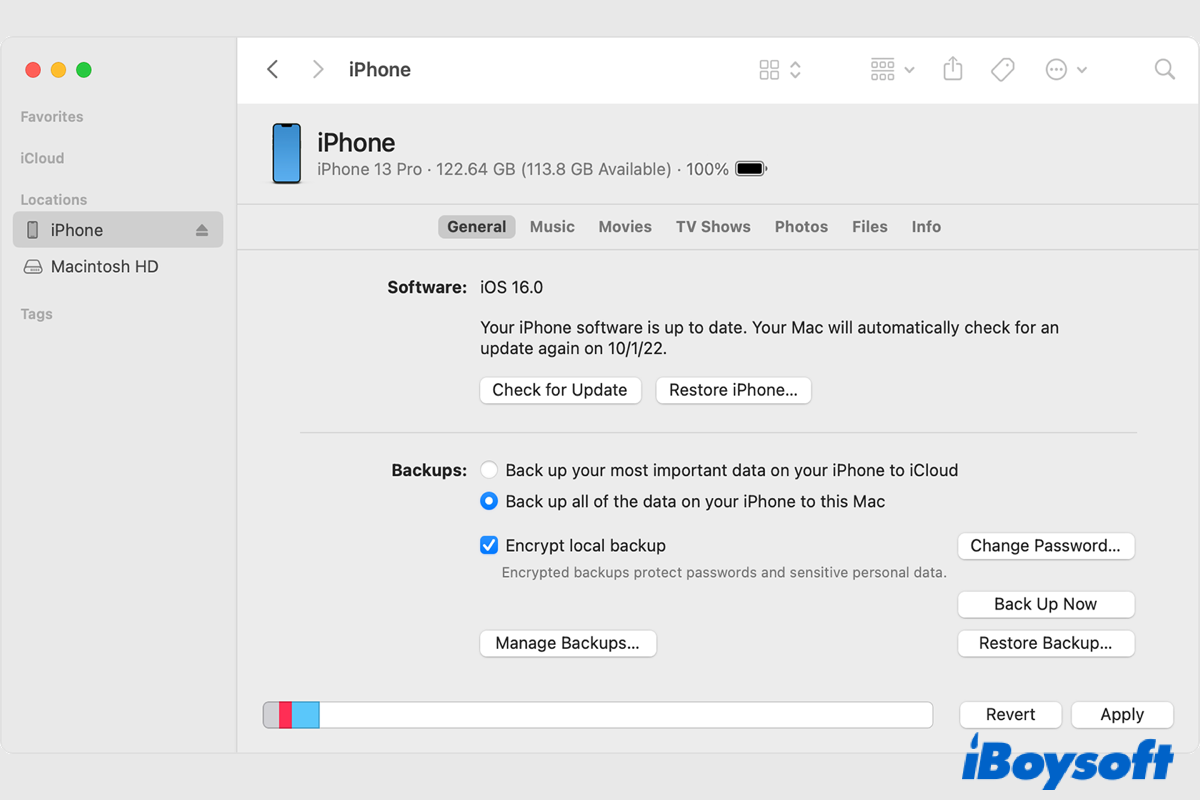
Encrypt Local Backup: An Option to Protect iOS Backup on Mac/Windows
This post explains the encrypt local backup option while backing up iPhones, iPad, and iPods to Mac/Windows, reading this post provided by iBoysoft to know how to use this backup encryption feature. Read more >>
Conclusion
Despite the fact that Apple iCloud itself possesses data encryption features, its protection ability isn't strong enough. iCloud users are still under various potential attacks, exposing their Apple ID and private iCloud data to cybercriminals.
If you want to keep your data fully under your control with flawless protection, an additional security layer is necessary. Third-party encryption applications can help. iCloud encryption applications safeguard your data through more advanced technologies and stronger encryption methods. With them, you can conveniently store, share, and manage your iCloud data.

Things You Should Know about OneDrive Encryption
This article introduces you MS OneDrive and how does it protect your files and folders. Read more >>