Have you ever used BitLocker on Windows? If you have, you must have heard of TPM, a hardware component installed in many newer computers by computer manufacturers. But do you know what it is? What are the major uses for TPM? And how it works with BitLoker?
If you want to know more about TPM, keep reading the following text; there is everything you want to know.
If you think this post is useful, share it with your friends.
What is TPM?
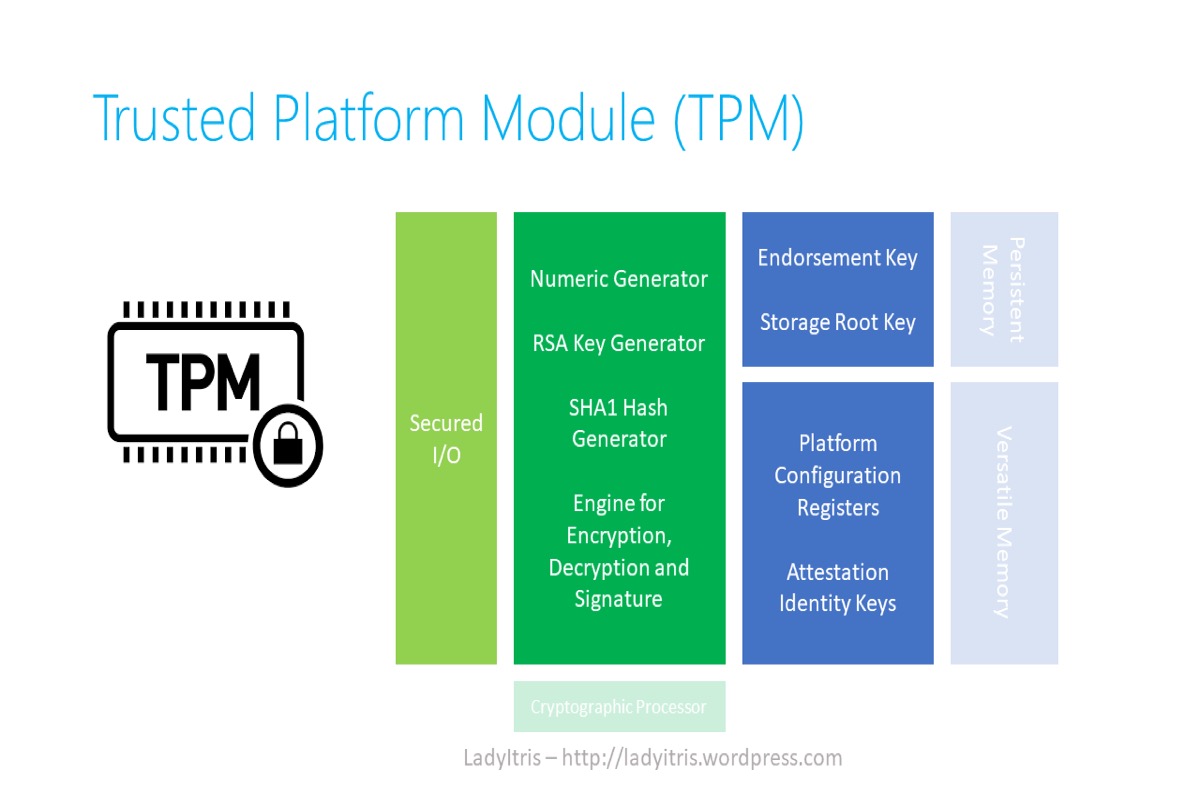
Trust Platform Module, abbreviated by TPM and also known as ISO/IEC 11889, is an international standard for a secure cryptoprocessor. It is used for Windows Defender, digital rights management (DRM), Windows Domain logon, protection and enforcement of software licenses, and prevention of cheating in online games.
TPM was conceived by TCG (Trusted Computing Group), whose members include Microsoft, Intel, Hewlett-Packard, IBM, and so on. And TPM Main Specification Version 1.2 was standardized by International Organization of Standardization (ISO) and International Electrotechnical Commission (IEC) in 2009 as ISO/IEC 11889.
TCG announced a major upgrade to their specification version entitled TPM Library Specialication 2.0 on April 9, 2014, and released in November 2019, called ISO/IEC 11889:2015. One of Windows 11's system requirements is TPM 2.0.

Don't forget to share this TPM's wiki with your friends!
Uses for TPM
Here introduces you to two major uses for TPM. But for most people, one of the most relevant uses for TPM is encryption.
Disk Encryption
For disk encryption, you may think of BitLocker, which is a full-volume encryption feature included with Microsoft Windows. BitLocker relies on TPM to allow the use of a key when startup occurs in an excepted way.
BitLocker can use TPM to protect the keys used to encrypt the computer's storage devices and provide integrity authentication for a trusted boot pathway that includes firmware and boot sector.
Platform Integrity
The primary use of TPM is to ensure the integrity of a platform, which means every computer behaves as intended. When TPM is used, the firmware and the operating system are responsible for ensuring integrity.
It is to ensure that the boot process starts from a trusted combination of hardware and software, and continues until the operating system has fully booted and applications are running.
TPM for BitLocker
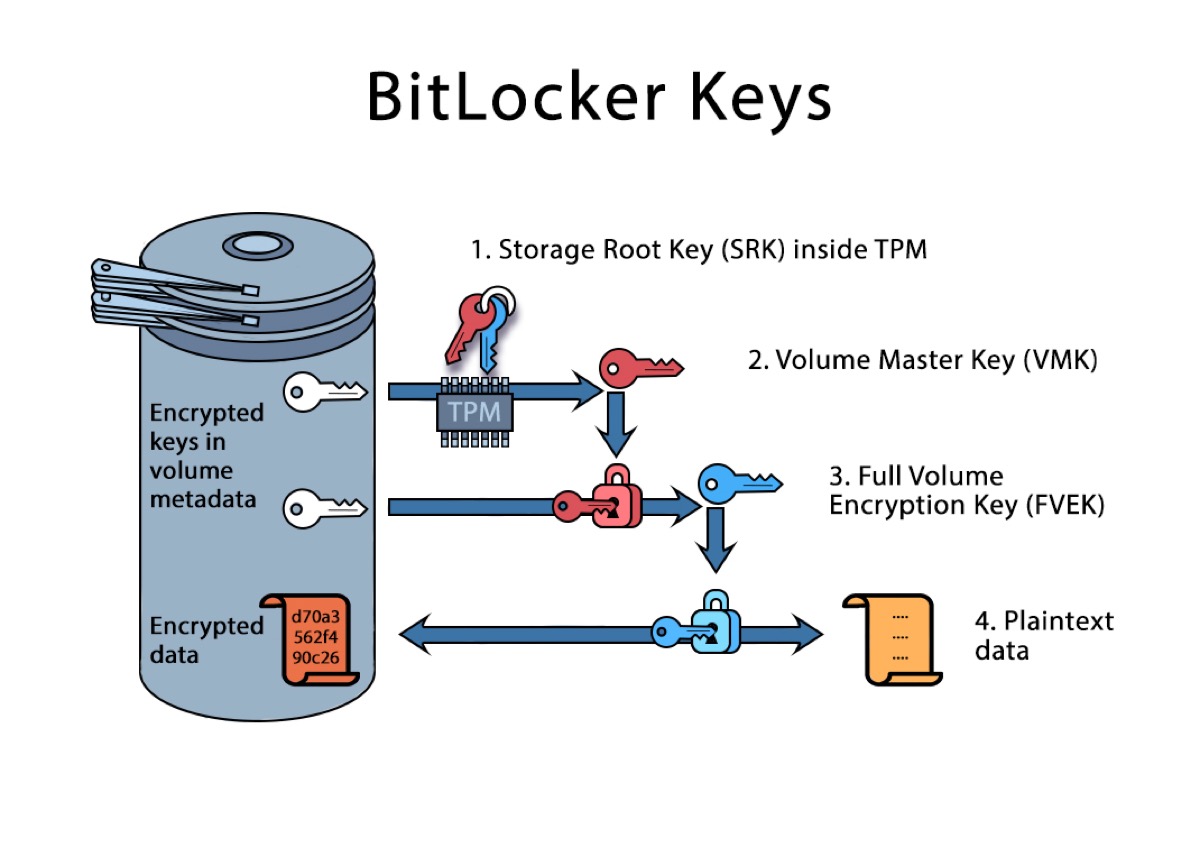
BitLocker provides maximum protection when used with a TPM version 1.2 or later versions. It works with BitLocker to help protect user data and to ensure that a computer hasn't been tampered with while the system is offline. Enable BitLocker disk encryption and Windows will use a TPM to store the encryption key.
You normally just gain access to an encrypted drive by typing your Windows login password, but it's protected with a longer encryption key than that. That encryption key is partially stored in the TPM, so you need your Windows login password and the same computer the drive is from to get access.

Read more: Format BitLocker Drive with or Without Password/Recovery Key
How to Find BitLocker Recovery Key And Do BitLocker Recovery Key?
Share this post with your friends to let them know more about TPM.
FAQ about TPM
- QWhat is Trusted Platform Module TPM used for?
-
A
A TPM is used to improve the security of your PC.
- QShould I turn TPM on or off?
-
A
For Windows 10 user, if you want to utilize the BitLocker data encryption feature, you must enable the TPM. For Windows 11, you won't even be able to install it unless the TPM is enabled.