In our work and study, maintaining privacy is important. With the proliferation of cyber threats, encryption has become an essential tool for protecting data. One of the most robust and widely used encryption methods is PGP, short for Pretty Good Privacy, in online communications.
What is PGP Encryption? Developed in 1991, the PGP Encryption tool is popularly used for email security. PGP gained traction because it was freely available, making it accessible to a broad range of users. And it combines symmetric encryption and public-key cryptography.
For those looking for enhance the security of the email communications, PGP presents a practical and affordable solution. This guide will walk you through the introduction of PGP Encryption and I hope that you can protect your messages effectively after reading.
How PGP Encryption works
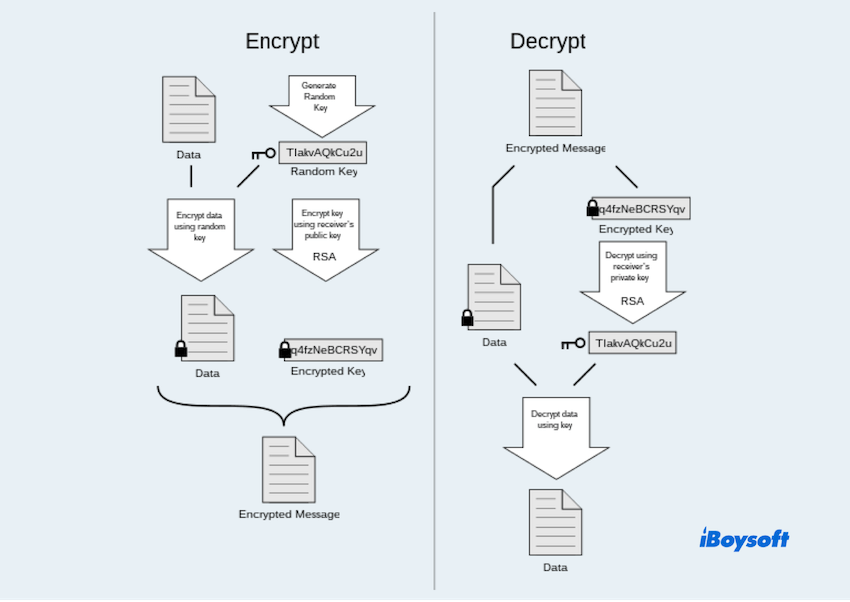
PGP Encryption operates by combining both public-key(asymmetric) and private-key(symmetric) cryptographic techniques.
- Key Generation: PGP creates a pair of keys—a public key and a private key. The public key is shared with others, while the private key is kept secret. This pair is unique to each user.
- Encryption Process: When a sender wants to encrypt a message or file, they use the recipient's public key to encrypt the data.
- Decryption Process: Upon receiving the encrypted message, the recipient uses their private key to decrypt the data.
Simply speaking, if you need to encrypt or decrypt, you and another user need to have the public key and private key both.
Now let's move to the applications and usages of PGP Encryption.
Examples and usages of PGP
Many places use PGP Encryption, let's have a look:
- Email Encryption: PGP is widely used to secure email communications. Many email clients, such as Mozilla Thunderbird with the Enigmail plugin, support PGP encryption, ensuring that emails are readable only by the intended recipient.
- File Encryption: Users can encrypt files on their computers to protect sensitive data. This is particularly useful for securing backups or storing confidential documents.
- Software Distribution: Developers often use PGP to sign software releases. This practice helps verify that the software has not been tampered with and originates from a trusted source.
- Secure Messaging: PGP is implemented in various secure messaging apps to protect the privacy and integrity of conversations.
Advantages and disadvantages of PGP
While PGP Encryption offers robust security, it also has its advantages and challenges. See them in the table and think twice:
| Pros | Cons |
| High security for strong algorithms and encryption | Too complex for non-technical users |
| Integrity and authentication with digital signatures | Too long for large file exchanges |
| Decentralized trust | Memorizing multiple keys is cumbersome |
If you think these points listed are useful for you, please share them with others.
How to PGP encrypt a file?
Encrypting a file with PGP can be done through various software tools and applications. Here's a simple guide on how to PGP encrypt a file using GnuPG on Mac Terminal:
- Finder > Applications > Utilities > Terminal.
- Type brew install gnupg then press the Enter key.
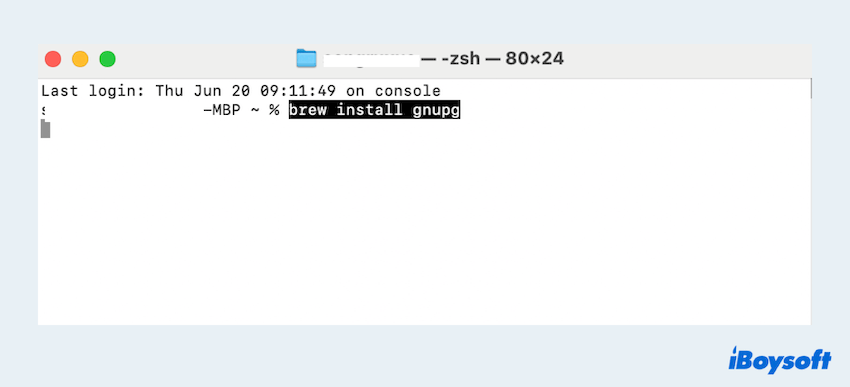
- Type gpg --full-generate-key then follow the prompts.
- Export your public key using gpg --armor --export [email protected] > publickey.asc.
(Replace [email protected] with your email address used during key generation.) - Share your public key.
This is just the encryption process, the recipient should decrypt the file with the public key. This basic guide outlines the core steps for using PGP.
For more advanced usage, you can explore additional options and configurations in the GnuPG documentation. Share this post to help people who want to use PGP Encryption. You can also learn how to encrypt a drive on Mac.
Conclusion
PGP Encryption remains a cornerstone of digital security, offering robust methods to protect and authenticate data. Despite its complexities, the advantages of maintaining privacy and security in communications and data storage make it an invaluable tool.
Whether you are securing emails, encrypting files, or ensuring software integrity, PGP Encryption provides a versatile and reliable solution to safeguard your information.