The "security policy would not allow process" error typically appears on systems like SELinux or Android. If you see this error on your Mac, it generally means that the system has blocked a potentially unauthorized action for security reasons.
So, how can you fix it? This guide will walk you through the steps to troubleshoot and resolve the issue. Keep reading to find the solution.
Why does "security policy would not allow process" appear on your Mac
macOS features multiple layers of security, including Gatekeeper, System Integrity Protection (SIP), App Sandbox, and the TCC (Transparency, Consent, and Control) system. These mechanisms work together to prevent unauthorized or potentially harmful software from running on your system.
When you attempt to run certain unverified apps, scripts, or command-line operations, macOS automatically enforces these security protocols to inspect the origin, permissions, and behavior of the process. If any potential threat or violation is detected, the system will immediately block the process from executing to maintain system integrity and protect your data.
Here are the most common causes of this error:
- Installing third-party software from unidentified sources.
- Running apps or scripts that are not signed or notarized by Apple.
- Accessing system areas protected by SIP (System Integrity Protection).
- Using AppleScript or automation tools without granting the necessary permissions.
- macOS Security & Privacy settings preventing the app from launching.
- Your Mac is managed by MDM (Mobile Device Management) or subject to enterprise policies that restrict certain actions.
Click the icon below to share the reasons with more people!
How to fix the "security policy would not allow process" error
When the “security policy would not allow process” error appears on your Mac, leaving it unresolved can disrupt critical tasks like backups, file synchronization, and other processes. But don't worry, below you'll find several effective solutions.
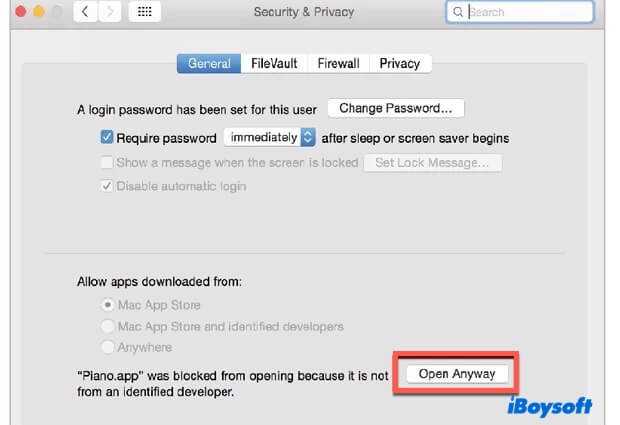
Allow the blocked app manually
macOS blocks unverified apps by default. This method lets you manually approve a specific app without changing system-wide settings.
You can go to System Settings > Privacy & Security. Scroll down and look for any message about a blocked app, and click “Allow Anyway” or “Open Anyway”.
Check the SIP (System Integrity Protection) status
SIP is one of the core security mechanisms in macOS, designed to prevent system files and critical processes from being tampered with. When you try to run certain processes that need access to protected system areas, such as /System or /usr (excluding /usr/local), SIP may block the operation.
This type of restriction is commonly encountered when using certain third-party tools, installation scripts, or command-line programs. If you're confident the operation is safe but it's still being denied, it's worth checking whether SIP is the reason.
How to Check SIP Status:
- Open Terminal.
- Enter the following command and press Return: csrutil status
- If the output says "System Integrity Protection status: enabled", it means SIP is currently turned on.
If you need to disable SIP temporarily, click here to learn how to disable SIP on Mac.
Warning: Disabling SIP reduces your system's overall security. This is only recommended for developers or advanced users in controlled environments.
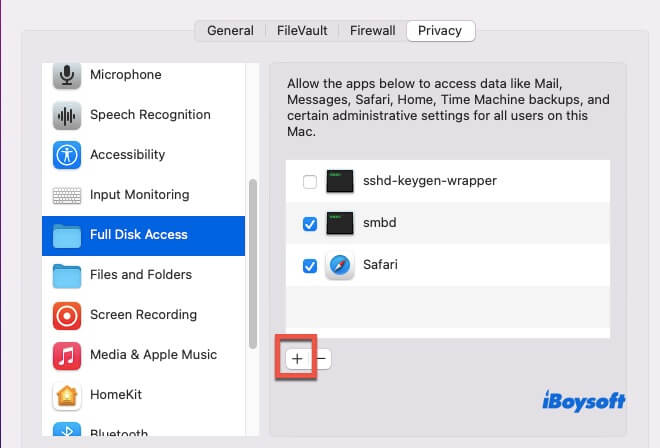
Grant Full Disk Access to Terminal
macOS's TCC (Transparency, Consent, and Control) system restricts apps from accessing sensitive files or directories. If your terminal or script tool doesn't have Full Disk Access, the system may block its operations, causing errors.
You can grant access by going to System Settings > Privacy & Security > Full Disk Access, then click the “+” button to add Terminal, iTerm2, or the app you use to run scripts (such as VS Code or Automator). After adding, exit the settings and restart the app for the changes to take effect.
Use spctl command to manually approve the app
You can use the spctl command in Terminal to manually add an app to the trusted list, bypassing Gatekeeper's default restrictions. This method is suitable when you're sure the software is safe but don't want to disable the entire security system.
- Open Terminal and run the following command to check if the app is being blocked: spctl --assess --verbose /path/to/your/app
- If it shows “rejected”, it means the app is blocked by Gatekeeper.
- Run the following command to allow the app to run: sudo spctl --add --label "MyApp" /path/to/your/app
Check for MDM restrictions
Company devices often enforce strict security policies via MDM. These may override personal settings and block scripts or apps.
So, go to System Settings > General > About > Management. If your Mac is managed, you can contact your IT department for help.
Share the above five methods to help more people!